Introduction
While the media highlights the increasing incidents of (allegedly) state-backed cyber-attacks, it seems the main source of threats is closer to home. The recent Clearswift 2018 survey shows that more than two-thirds of all incidents arise from within an organisation. These figures (except USA) are slightly down from their 2017 highs, but still depict a large percentage of a growing problem.
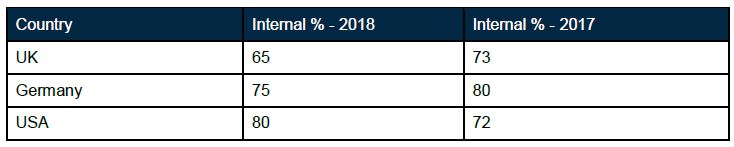
Before we look at what can be done to try to limit the impact to an organisation, it is worth remembering that the majority of these ‘insider threat’ data breaches are due to carelessness or negligence, rather than from any malicious intent.
The latest Ponemon study of 159 organisations (18% from the financial services sector) with over 1,000 employees, each of whom had suffered at least one data breach over the 12 months to January 2018, found that the negligent insider was the root cause of most incidents:
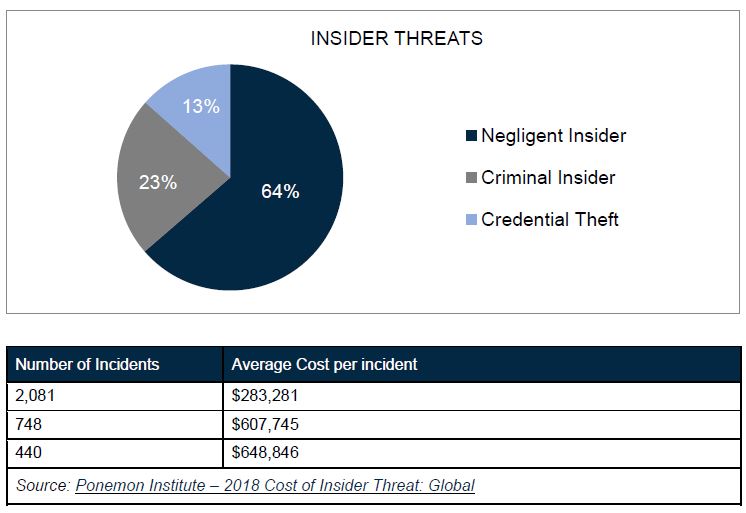
The survey found that it takes, on average, more than two months to contain an insider incident, with only 16% contained in less than 30 days. So, if it takes such a long time to contain an incident, and has such a large cost to an organisation, what can be done to help prevent incidents or mitigate their impact?
Education
The following sections will provide a number of available preventative steps, but the key one is to get employees to understand that data security is a critical issue for your business.
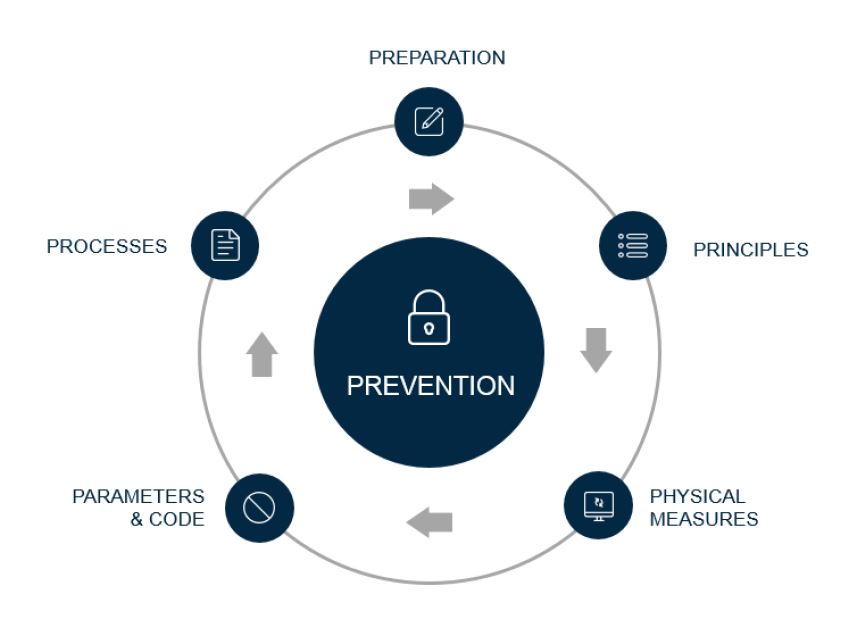
Preparation
A good first step is to review and categorise an organisation’s data to determine how much data is held, where it is located and the different types of data that will require varying levels of protection. The categories used could be as simple as:
- Public – data generally available
- Internal – data used within the organisation and company confidential
- Restricted – more sensitive data requiring greater control
Secondly, determine how the data is used; e.g.
- Marketing
- During company business processes
- HR and payroll purposes
The third step is to record where the data is used, for example this could be:
- Within the Company offices
- Externally, on company laptop PCs
- Externally via a Company cloud
- Externally, at sub-contractor sites
Principles

A documented set of data principles will remove any ambiguity around what actions are permissible.
While most data can be viewed as Company Confidential, within the company it could be worthwhile circulating information on a ‘need to know’ basis. This would limit the possibility of information being obtained by external resources, present within the company environment, or by staff who may not realise the importance and therefore the secrecy that should be employed. Some industries have virtual barriers, or Chinese-walls, beyond which data should not pass for conflict of interest or client confidentiality purposes.
When setting up systems to handle the flow of information, it is useful to adopt the principle of Least Privilege, under which a base level of data access is initially provided, with any additional levels of access provided only if necessary for an individual’ s work role.
Other ‘Good data habits’ that are widely adopted include:
- Not sharing or having group passwords
- Making Passwords difficult to crack, and changed on a regular frequency
- Keeping work-data ‘at work’
- Locking a computer when leaving a work station
- Keeping desks clear of clutter and printed documents, particularly overnight
Examples of strong passwords will:
- Be as long as possible, but still memorable
- Contain lower and upper-case letters, numbers, special characters and punctuation
- Not contain any obvious or familiar names (such as pets) that would be easy to guess
- Be used for single applications or websites
Consider using a Password Manager application if a large number of passwords need to be remembered.
Physical Measures

With the preparation done and principles in place, attention can turn to measures that would prevent data breaches. Physical measures can block access to data following an act of carelessness, such as a lost laptop, or credential theft, malicious external attempts to gain unauthorised entry. Typical physical blocks include:
- Disk encryption, to prevent unauthorised access to a lost or stolen device
- Employing 2 factor authentication, e.g. a Password plus Remote Access codes (via a token) so that two devices are needed in order to get access
- Virtual Private Networks (VPNs) to prevent data being stolen en route to a business environment, by using an encrypted ‘data tunnel’
- Firewalls to block unauthorised system access from external devices
- A block on removing data from the work environment, via the use of remote/mobile devices
Parameters & Code

In addition to physical blocks, it is possible to set up software blocks to protect an environment. These could be via parameter settings, or by the use of software applications.
One such block is called Access Control, which limits the users who are able to access particular areas of data. Each area has an owner who must authorise and control the access of other users.
A second block is called Segmentation, which is the division of a company’s data into sets or segments that are held separately. Any loss of data following a breach is then restricted to the data that was in the affected area, and not the whole environment.
A third type of block is to ban access to particular internet locations, e.g. Social Media sites, or the use of particular applications, e.g. Instant Messaging. Blocking these communications media attempt to prevent information being passed or sought through non-business medium.
A final set of software designed to prevent data breaches is called Anti Virus software, which is used to stop the spread of malicious Malware, Ransom-ware, Impersonation, Spear-Phishing, etc. It does this by comparing stored files and incoming messages (e.g. email) with known virus patterns and quarantines anything that matches.
Software can also be used to monitor systems and use behaviours etc, to spot when unusual or unauthorised activities are taking place. These include modern Data Leak Prevention, ‘Insider Threat Programs’ and AI tools that can detect if a user is behaving in an unusual manner, when perhaps under duress. Such tools are in their infancy, but will quickly develop to provide an extra layer of data protection.
Processes

In addition to Physical and Software measures to prevent data breaches, the following processes are commonly employed to reduce the likelihood and impact of data breaches.
Performing Background checks on would-be joiners can identify potentially dangerous individuals before they become employees who are given access to company data. Similar checks should be performed on contractors and other third-party users of the company systems to prevent data leaks.
Once on board, it is essential that all employees and contractors undergo regular education courses focusing on the security measures employed to protect company systems, data and personnel from a cyber attack. These should highlight the need to be vigilant and to report any suspected threats or data breaches.
Where sensitive data is being processed or distributed it is common to encrypt the file content to prevent it from being seen, or amended, by unauthorised users.
The use of a verification stage or 4-eyes check, on outgoing messages can prevent them from containing inappropriate content or being sent to incorrect recipients. Such checks are common where financial payments are being processed.
Having defined ‘Exit’ procedures also reduces the likelihood of data breaches. These should include the prompt blocking of physical and system access, together with the return of company devices, documentation and data. Changes to system passwords or other known information should also be performed.
Conclusion
The numbers for all types of threat incident are increasing. While breaches due to insider threats have reduced as a percentage of the overall total, the actual number is still growing and still accounts for 2-4 times as many breaches as external causes.
Of the internal threat total, two thirds are caused through accidental or careless behaviours by staff. Therefore, while it is important to have in place the Principles and Processes; and the Physical and Software blocks mentioned above, it is key to get staff ‘buy in’ to them. Without this, corners will be cut; controls by-passed; and mistakes made/covered up. It is essential that staff fully understand the need for the data protection mechanisms and ‘live them’ during their work life. There is no better source of data security process improvement, monitoring or reporting than the staff themselves, when they understand the need for data security.
About the Author
Graham Stroud is a Principal Consultant at Mansion House Consulting with over 30 year’s leadership, programme management, change management and process re-engineering experience in the Financial Services sector.
About Mansion House Consulting
MHC is an international business and technology consultancy, focused exclusively on the financial services sector. We provide high quality, practical and robust solutions for the industry through our team of highly experienced consultants and subject matter experts.
We specialise in change and transformation management, toolkits, regulatory and governance frameworks. We deliver solutions globally to the transaction and investment banking communities, including leading Tier One clients from the financial services industry.
Established in 2009 we have been expanding and evolving ever since, with a team in excess of 300 and listed in the Sunday Times Tech Track 100 on four consecutive years 2013-2016, the Investec Mid-Market 100 list in 2016, the London Stock Exchange’s 1000 Companies to Inspire Britain 2015 and 2017, The Financial Times FT 1000: Europe’s Fastest Growing Companies 2017 as well as The Financial Times FT Future 100 UK. Headquartered in London, we have a global presence through offices in Sheffield, Manchester, Frankfurt, Singapore, New York, Jacksonville (Florida) and Bangalore (India).
To find out more about our services, explore our website www.mansion-house.co.uk or contact:
+44 (0)20 3697 7140
Disclaimer
This publication has been prepared for general guidance on matters of interest only, and does not constitute professional advice. You should not act upon the information contained in this publication without obtaining specific professional advice. No representation or warranty (express or implied) is given as to the accuracy or completeness of the information contained in this publication, and, to the
extent permitted by law, the Mansion House Consulting Limited Group, its members, employees and agents do not accept or assume any liability, responsibility or duty of care for any consequences of you or anyone else acting, or refraining to act, in reliance on the information contained in this publication or for any decision based on it.
© 2018 Mansion House Consulting Limited. All rights reserved.
In this document, “MHC” refers to the UK entity, and may sometimes refer to the MHC group network. Each MHC entity is a separate legal entity. Please see www.mansion-house.co.uk for further information.




